Data security service
-

Service Description
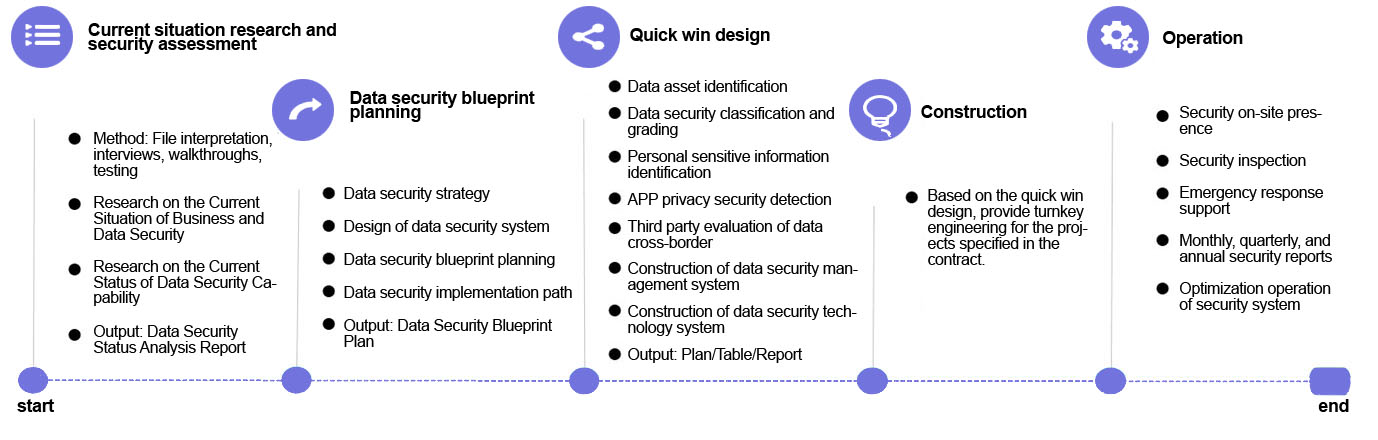
Xinzhi Technology covers all aspects of data security projects, including research, planning, design, security construction, and security operations. All work can be independently completed by Xinzhi Technology, and it continuously deepens various aspects of project management and technical implementation, iteratively optimizing based on customer feedback.