Security Hosting Service Solution
-
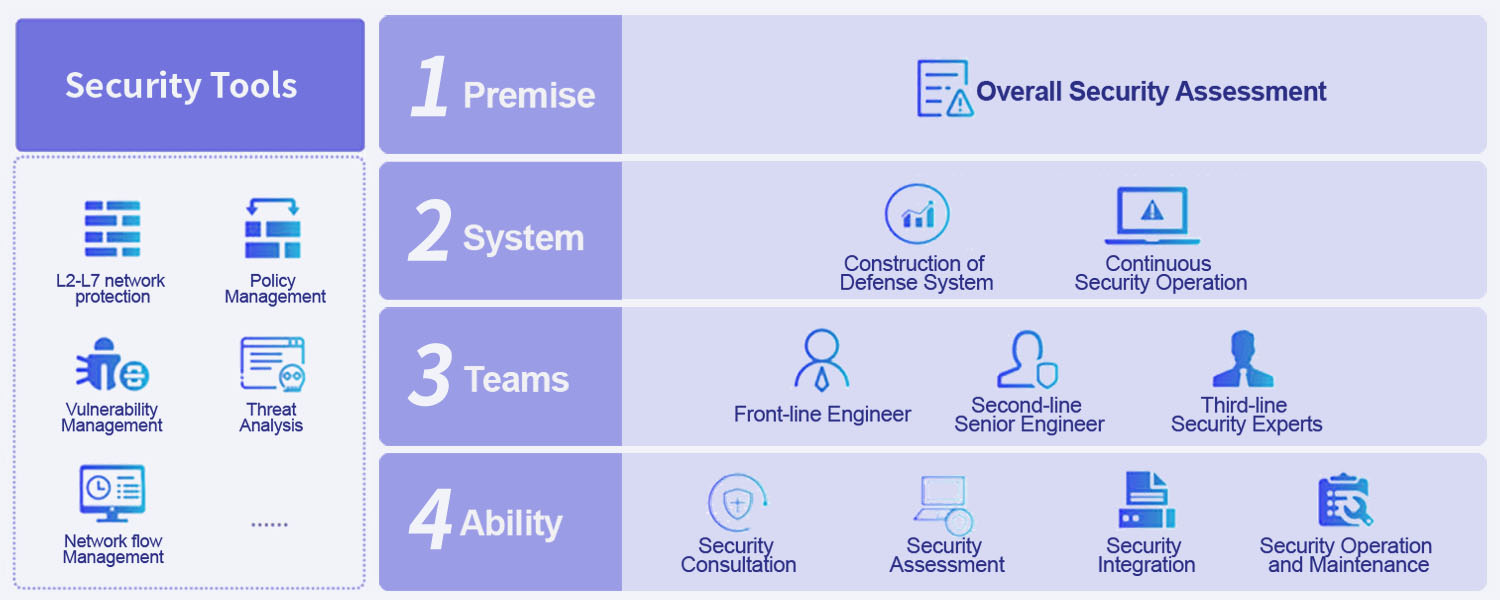
Overall architecture
Xinzhi Technology's security hosting service emphasizes human-machine intelligence within the framework of an adaptive security architecture, using self-developed and industry-renowned products as security support tools. Based on a comprehensive assessment of security risks and an overall improvement in defense capabilities, the service focuses on asset management, vulnerability management, and security event detection and response, continuously monitoring the security risk status of the enterprise while coordinating with the enterprise's security business processes to integrate technology, processes, and Organic integration of people ensures a closed loop of enterprise information security.
