cybersecurity consultation service
-

MPLS consulting service
MPLS consulting service
Relying on Xinzhi Technology's experience in security compliance and consulting services, through complete one-stop security consulting + security construction services of MPLS 2.0, combined with the technical concepts of "one premise/two systems/three-level teams/four capabilities" and "one center, three layers of protection", we help customers build a security system suitable for their own business characteristics, and pass the evaluation of graded protection professionally and quickly.
-

Critical Information Protection Consulting Services
Critical Information Protection Consulting Services
Xinzhi Technology provides an integrated network security defense system for key infrastructure for important industries and fields such as public communication and information services, energy, transportation, water conservancy, finance, public services, e-government, etc. in accordance with 《Regulations on Security Protection of Key Information Infrastructure》 and 《Basic Requirements for Network Security Protection of Key Information Infrastructure of Information Security Technology》
-

Password evaluation consulting service
Password evaluation consulting service
It is a process for the security team of Xinzhi Technology to evaluate the compliance, correctness and effectiveness of the password application of the network and information system using commercial password technology, product and service integration.
-

Communication protection consulting service
Communication protection consulting service
Xinzhi Technology follows the requirements of the 《Management Measures for Communication Network Security Protection》, evaluates the communication network security protection work of the communication network operation unit, and verifies whether its communication network unit meets the regulations of the telecommunications management organization and the communication industry standards.
-

Interpretation of laws and regulations
Interpretation of laws and regulations
The security expert team of Xinzhi Technology provides interpretation and interpretation of laws and regulations such as the Cybersecurity Law, Data Security Law, and Personal Information Protection Law for enterprises and institutions, and identifies compliance risks based on the current situation of information security in enterprises and institutions.
-

Industry Policy Interpretation
Industry Policy Interpretation
The security expert team of Xinzhi Technology is proficient in mastering the information security construction standards and policies released by various industries, and provides analysis and interpretation of relevant requirements for enterprises and institutions. Based on the current situation of information security in enterprises and institutions, identify gaps and propose improvement suggestions.
-

ISO27001 Consulting Service
ISO27001 Consulting Service
With a full understanding of the requirements of the ISO/IEC27001:2022 information security management system, the Xinzhi Technology Security Expert Team assists enterprises and institutions in formulating information security policies and strategies, clarifying management responsibilities, selecting control objectives and measures based on risk assessment, and achieving a dynamic, systematic, all staff participation, institutionalized, and prevention oriented information security management approach for the organization.
-

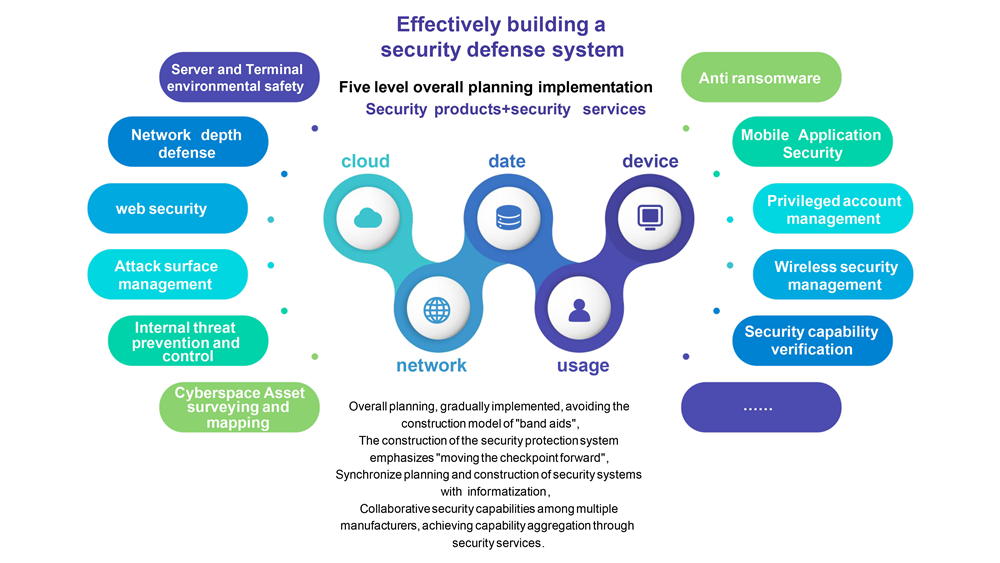
Cybersecurity System Planning
Cybersecurity System Planning
Based on the analysis of the overall plan for information security risk assessment in enterprises and institutions, Xinzhi Technology proposes the overall plan, goals, and basic principles of information security technology work, and plans the future information security overall architecture from the perspective of information security guarantee system.